Philippe GUARNIERI
Cyber security, Risk Management
Professional Status
Employed
Open to opportunities
About Me
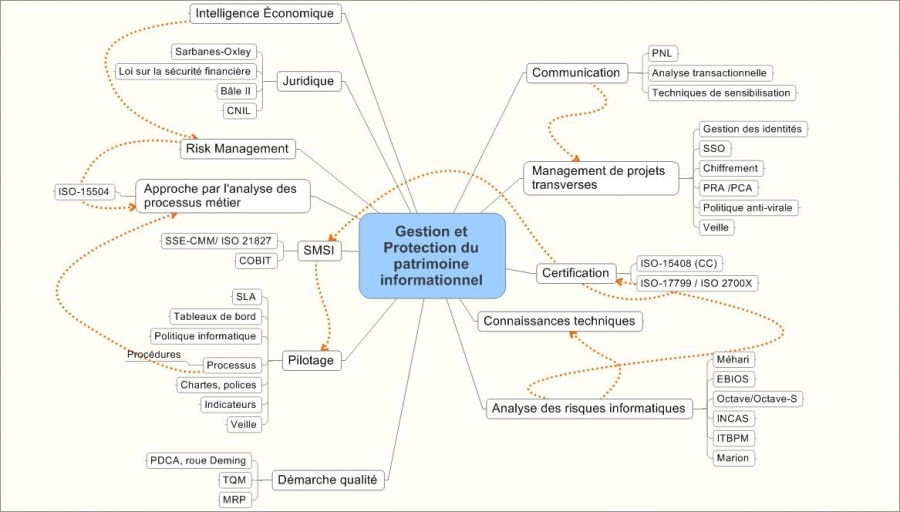
Holistic Risk Management digital safety and security, strategy development, implementation of action plans, organization, governance.
Tools, methods, management, monitoring, quality of the level of security: BSC, ISMS, dashboards, of governance.
Risk management related to a process approach, Intelligence.
Management techniques and cross hierarchical methodology and experience of complex projects, organizations, cross-sectional and functional relationships, sometimes with a strong international dimension, live, teams of 4 to 80 + people.
Assistance with CSO
Seminars and training to the security of information systems.
Construction of technical proposals, outsourcing, missions, pre-sales consultant, webmarketing.
Tools, methods, management, monitoring, quality of the level of security: BSC, ISMS, dashboards, of governance.
Risk management related to a process approach, Intelligence.
Management techniques and cross hierarchical methodology and experience of complex projects, organizations, cross-sectional and functional relationships, sometimes with a strong international dimension, live, teams of 4 to 80 + people.
Assistance with CSO
Seminars and training to the security of information systems.
Construction of technical proposals, outsourcing, missions, pre-sales consultant, webmarketing.
Security Program Manager
DXC Technology
April 2017
to November 2020

- The security program manager is responsible for all program management tasks.He is is expected to define the standards, tools and governance required to effectively manage and control the security program.The person filling this role leads the program team, assigns tasks, monitors deliverables and schedules, and interfaces with other groups as needed.He or she also provides direction to the projects in the program and ensures that they meet all scope, time, budget and quality expectations.
Security Program Manager
HP
January 2014
to March 2017
Grenoble
France

- The security program manager is responsible for all program management tasks.
He is is expected to define the standards, tools and governance required to effectively manage and control the security program.
The person filling this role leads the program team, assigns tasks, monitors deliverables and schedules, and interfaces with other groups as needed.
He or she also provides direction to the projects in the program and ensures that they meet all scope, time, budget and quality expectations.
Account Security Officer
Hewlett Parckard
Since March 2012
Grenoble
France

- Compliance, quality, and optimization
Security governance, compliance, and operations
Creation, implementation, and optimization of processes or standards
Management of the security and compliance risks, ensuring that contractual security commitments are met
Audit facilitation, tracking, remediation, and follow-up
Sustained and continuous delivery excellence in IRM operations (including margin protection, avoidance of non-performance and non-compliance contractual penalties)
Relationship management between HP ESS suppliers and the client, overseeing multiple third party services
Identification of additional services and revenue generation for HP
Consultant
reseau des entreprises
2007
to March 2012
Freelancer
Grenoble
France

- "Network specializes in entrepreneurship, management and
the organization "
Various missions: Computer security and Risk digital IT projects, WEB 2.0, Social Networks.
Leader
Clusir
January 2007
to April 2010
Grenoble
France

- The animation of CLUSIR put me in a close relation
to specific security concerns of IT managers,, in addition to a proactive approach towards business, i had established a strong network. " - commercial experience of: prospecting, making appointments, meeting, persuade, lead, enter into partnership
Deputy Head of the Information System Security
ADP-GSI
February 2001
to September 2006
Full-time
Grenoble - Paris
France

- Experience in an American group specializing in human resources beyond its growth was very informative because of its multicultural
- Establishment of an organization's computer security management information system
Chief Security Officer
Schneider Electric
January 1991
to February 2001
Full-time
Grenoble
France

- The operating rules of a large group is very special and this experience helped me to understand the subtleties.
- Manager IT Services
- Establishment of an organization's security management information system
It Manager
Alsthom
January 1990
to December 1990
Full-time
Macon
France

- Industrial group with its traditional values, the first experience in an industrial environment
- It Management services
Technical and Production IT Manager
France TELECOM
January 1984
to December 1989
Full-time
Marseille
France
- In this subsidiary of FRANCE-TELECOM specialized in banking (products and services), I was able to read the particular constraints of the financial world
Studies on the structure of DNA via Braggs laws and vector analysis. Variations on the experiences of the Watson and Crick double helix (DNA).
- Governance and management of information security by an approach from end-to-end of the protection of the information assets of the company.
- Usage of the risk management as a strategic tool in correlation with the "Balanced-Scorecard(BSC)" and the strategic maps.
- Solid experience of the relationship with the trades, sense of service.
- Maieutics, organization of seminars.
- Information security training.
- NLP, transactional analysis.
-
ISM3 ISM3-SOMA: the process approach.
Mehari, SLA, TQM, PDCA, processes, CMMI, ITIL, MRP, COBIT, RISK-IT, VAL-IT, ERM, ISO2700x,ISO21827,ISO31000, Sarbanes-Oxley, EBIOS, OCTAVE, SSO, PKI, PGP, SSL, DRP, KPI, encryption, LDAP, architectures, identity management, regulatory constraints .
-
Good knowledge of development issues subject (2 UML, design patterns.
Java, EJB, Struts, Eclipse, Tomcat, DOT.NET, C #)
Web development technology marketing, communication (HTML, CSS, Flash, Ajax
Dreamweaver, web design, SEO)
CMS: Drupal, Plone, Joomla.
Operating systems (Windows, Linux, JBOSS, Apache, Tomcat, IBM mainframe ..)
ACF2, Top Secret, RACF, TCP / IP, SNA.
Good knowledge of tools and virtualization architectures n / 3.
- commercial experience of: prospecting, making appointments, meeting, persuade, lead, enter into partnership
- webmarketing
-
English reading and writing (international projects in English)
German School - Chinese Beginner